By now, we all know about scam or fraudulent emails. They’re a tried and tested tactic of cybercriminals worldwide. Luckily, they are also usually very easy to spot. These email messages are often full of typos and other tell-tale signs. Today, however, we’re going to talk about a form of spam that isn’t as easy to spot: email spoofing.
But what exactly is email spoofing, and how can you protect yourself against this tactic? We’ll explore that and more below.
What is Email Spoofing?
Email spoofing is a form of scam that impersonates a secure email from trusted sources or seemingly legitimate domains.
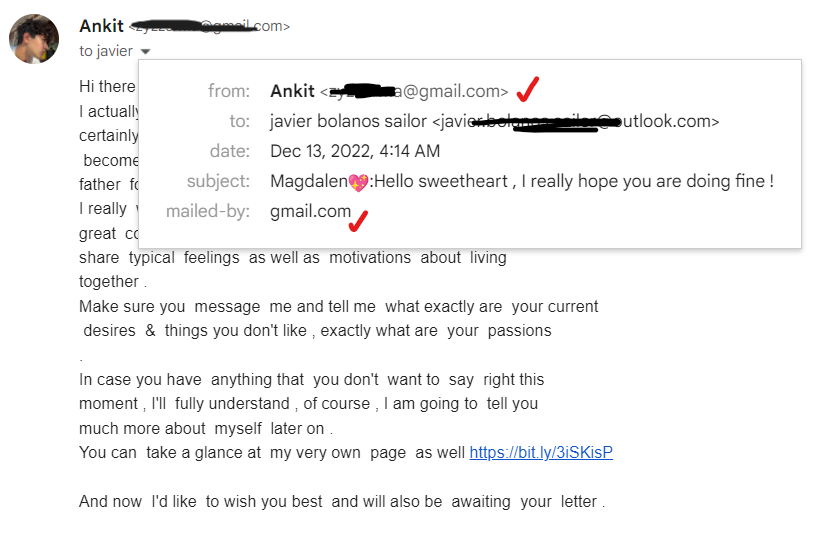
It’s a tactic that most people have been targeted with at some point. You’ll receive a message from an email sender that seems to be from a company that you know, but something feels off. Whilst some of these fraudulent emails are more convincing than others, usually, on closer inspection, you’ll realize that the email client is wrong.
Alternatively, you might get an email from a friend. Again, something feels wrong. They’re using language that they wouldn’t normally use and asking unusual questions. You find that the sender’s address isn’t the one they usually write from. These are both examples of spoofed emails.
Unfortunately, not everyone is able to spot these spoofed email messages. Some people may even reply with sensitive information or follow malicious links to fake websites (remember, just because a URL ends with .com, .ai, or .ca doesn’t always mean it is legitimate), falling for these all-too-common types of phishing attacks.
As we’ll explore later, there are many different motivations behind email spoofing. But in every instance, the user loses out to the scammer.
How is Email Spoofing Different from Phishing?
Firstly, it should be recognized that spoofing is a subset of phishing. The goal of a standard phishing email is to gain information from a user.
Phishing can occur via email, social media, or text. You might be informed you’ve won some money and need to reply with information to receive the gift. Phishers aim to get details such as login credentials from a user.
Phishing can be one of the goals of email spoofing. A scammer may send a spoofed email in the hope of obtaining a user’s password and other details.
Motivations Behind Spoofing
Aside from phishing, there are several other reasons scammers use email spoofing as a tactic. We’ve listed some of the motivations below:
- Spreading malware. One of the main reasons behind spoofing attacks is to infect a user’s device with malware. This is software that is created to damage or gain access to a PC. A spoofed email message will contain a file that has malware. Once the intended recipient downloads the file, their device will be infected;
- Damaging sender reputations. Spoof emails are sent under the guise of another user or organization, typically domains or email providers with a good domain reputation. Using these, scammers can bypass spam email filters that take domain reputation into account when filtering emails, increasing the chances of inbox delivery. Even more directly, this action can be used to damage the domain’s reputation by sending unprofessional, rude emails;
- Avoiding block lists. A spoofing attack might be a tactic used by people who are banned from communicating with certain users. Because they are not using their own email address, they can bypass spam filters;
- To remain anonymous. Another one of the most common reasons for email spoofing is for scammers to conceal their true details. This allows them to carry out malicious activities under the cover of anonymity.
The Three Types of Spoofs
Not all spoofing emails are the same. Scammers use different tactics to trick users. Let’s look at three different forms of email spoofing.
Domain Spoofing
With this form of email spoofing, a scammer can actually manipulate the ‘from’ field of an email, essentially resulting in a forged sender address. By doing so, an email will appear to have been sent from a legitimate source. This is a dangerous form of spoofing, as it’s harder to identify than other forms.
Display Name Spoofing
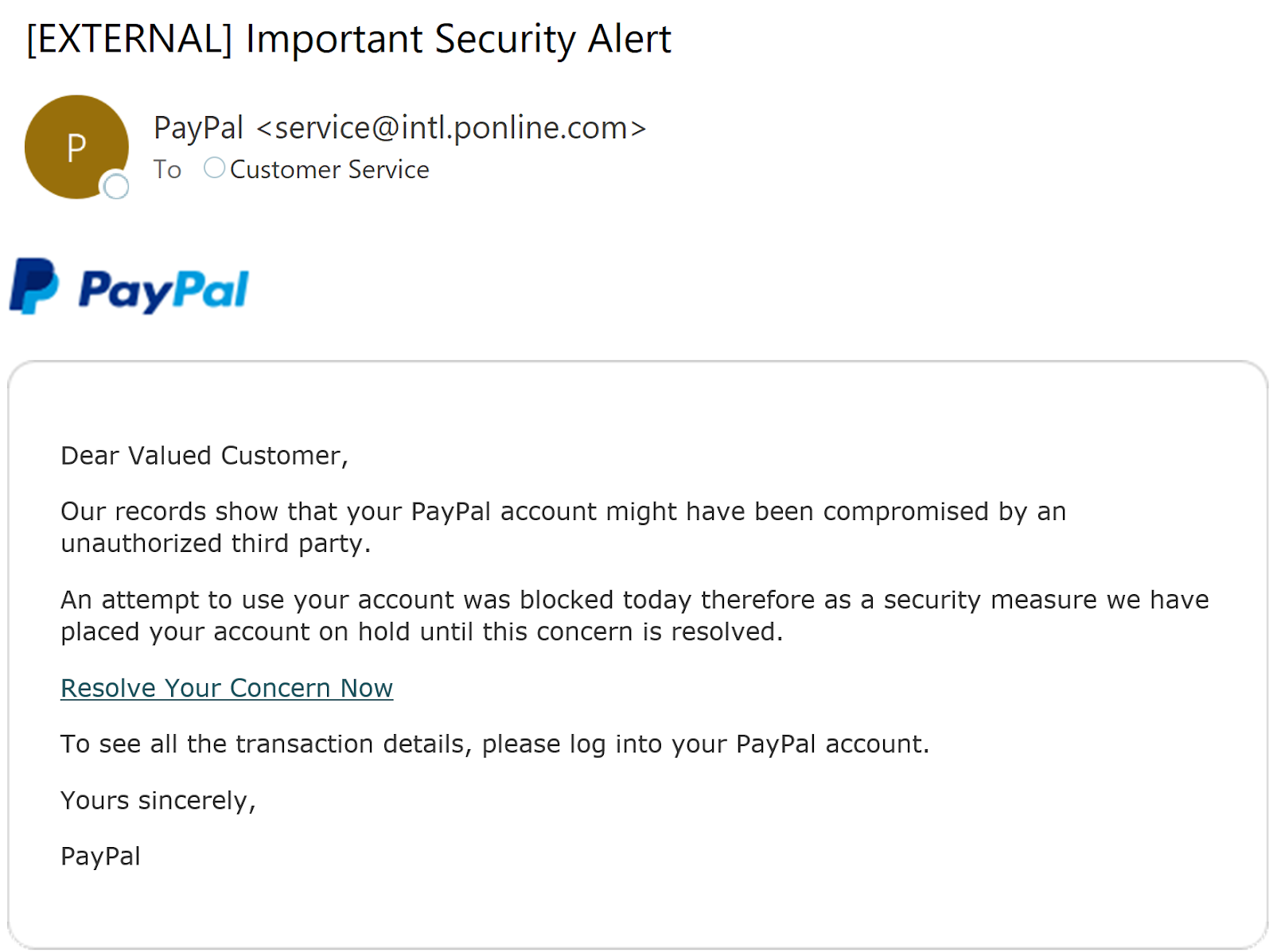
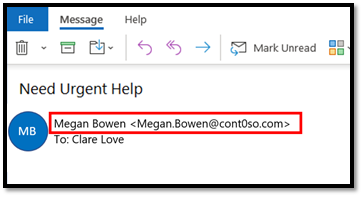
This type of email spoofing involves displaying a falsified name on an email message. For example, whilst an email might show as being from a familiar person or organization, it’s actually a scammer. Display name spoofing doesn’t change the sender’s address. A recipient will be able to identify an email as false if they look carefully.
Lookalike Spoofing
This tactic involves scammers using an address that looks similar to a legitimate email. For example, instead of ‘ebay’ an address and maybe even the email header might say ‘eb3y’. Or, the scammers may substitute Latin letters for visually similar Cyrillic or Unicode characters. A common example is when the lowercase “a” in an email address is substituted for a Unicode character closely resembling that its Latin counterpart. If a user only glimpses the address, they might not notice the difference.
How to Identify Spoofing Emails
As more and more people gain access to the internet, email spoofing is becoming one of the most popular types of phishing attacks. It’s important that you’re able to spot email spoofing if you ever receive a message that feels “off”. Below, we’ve compiled some of the best ways to spot a spoofed email.
Drastic Messaging
Scammers don’t want users to think too much about their messages. They want to influence users to take quick action before they can think about the consequences. That’s why email spoofing usually tries to invoke a sense of urgency.
A spoofed email might feature email headers such as ‘Response required immediately’ or ‘Important’. A common tactic is to threaten negative repercussions if a user doesn’t take action quickly. For example, an email might threaten to close a user’s account if they don’t log in.
False Email Addresses
Always check the email address of the sender before responding. Email spoofing aims to trick you by impersonating a trusted source or a legitimate sender. The email might even appear under the correct name. They can’t, however, replicate another user’s email address entirely.
Let’s imagine that a scammer is trying to impersonate PayPal. Whilst an email might say ‘PayPal’ on it, the email address might actually be ‘spfr2013qz7@nomail.com’. A user can avoid being scammed by simply checking the email address.
An Email is Asking for Sensitive Information
Credible organizations will never ask for sensitive information via email. And if you’re unsure, you can always contact an organization directly and ask about a message. Most companies will use a call center service company or a CCaaS provider, as explained by GetVoIP, that you can contact.
If you get an email asking for passwords or other information, it’s most likely a spoofed message.
How Dangerous is Email Spoofing?
Email spoofing can be extremely dangerous. At best, your reputation could be damaged, at worst, you might have your identity stolen. The only way to avoid these scenarios is by preparing. Here are some ways you can protect yourself online.
Keeping Your Online Identity Safe
There are steps you can take to avoid falling prey to identity theft as a result of spoof emails. Make sure you always stick to the following tips:
- Never include sensitive information in your emails;
- Take time to verify links before clicking them, even if you’re confident that a sender is legitimate. Take a careful look at the URL and see if there are any mismatches. For example, the URL might say .com instead of the .io domain name you were expecting to see;
- Never enter sensitive information on unsecured websites (secure pages start with ‘https’ and contain a padlock);
Ensuring the Security of Your Emails
Cybercriminals look for an unsecured email account that they can use for underhand purposes. Let’s explore some of the steps that you can take to make your account more secure:
- Always opt for a strong password (around 12 – 14 characters, and containing upper and lowercase letters, numbers, and special characters). For maximum password security, you can download a password manager;
- Add two-factor authentication to your account. This requires a code when you log in, which can be obtained via text or app;
- Keep your browser up-to-date. Outdated browsers are easy targets for hackers, always make sure your browser is up to date;
- Use an email security tool. These help detect and prevent threats more quickly.
Also read: What is Email Security? – Definition & Best Practices
Preserving Your Reputation as a Sender
As mentioned, one of the goals of spoofing can be to damage your reputation. If you’re a public organization, make sure to list your emails clearly on your website.
Consider whether you want to use free email services providers or paid services that have advanced security settings. Finally, remind subscribers about the risk of spoofing and allow customers to report any spoof emails they receive.
It’s important that you take action as soon as you become aware of spoofing. Inform your contacts that someone is posing as you and ask them to report any spoof emails they receive.
When you collect email addresses of potential clients or individuals interested in your services, you hold a responsibility to safeguard their data. Building a comprehensive email list not only ensures effective communication but also signifies your commitment to protecting the information entrusted to you.
How to Protect Your Domain Against Email Spoofing (Technical Precautions)
We’ve looked at some of the steps that you can take to secure your emails. Now let’s consider some security measures you can set up to prevent your domain from being spoofed:
DomainKeys Identified Mail (DKIM)
DKIM is an email authentication protocol that uses public cryptography to verify that an email hasn’t been modified between leaving the sender and arriving with the recipient. Essentially, your private key is matched to the recipient’s public key, enabling receivers to verify that the email is unchanged and was written by you.
To set up DKIM, you need to establish the fields that should be included in your DKIM signature, such as your “from” address, subject line, email body, etc. From there, a DKIM record will be created, which stores the public key that the email server uses to authenticate the email’s signature.
Sender Policy Framework (SPF)
SPF is another email authentication method. It specifies the mail servers that are authorized to send emails from your domain. Any email service receiving an email from domains or IP addresses not listed on your SPF record will be marked as spam.
To set up SPF, you need to create an SPF record for your domain that specifies all of your allowed servers and third parties. From there, add the SPF record to your domain provider as per their instructions.
Domain-Based Message Authentication, Reporting, and Conformance (DMARC)
DMARC builds on the existing DKIM and SPF protocols to provide added protection against spoof emails. Essentially, DMARC is a message directed from the sender of an email to the receiver, clarifying that the email is protected by DKIM and SPF. It also includes instructions that advise receivers on the appropriate action should the message not pass DKIM and SPF checks.
On your domain provider, set up a mailbox for DMARC reports and define your DMARC policies and reporting records.
Email Spoofing Statistics
If you’re still unconvinced about the dangers of email spoofing, just take a look at the statistics:
- Phishing is the most popular form of cybercrime. There are 3.4 billion spam emails sent every day.
- More than 300,000 Americans are victims of phishing each year;
- In 2022, 5 billion malware attacks were detected worldwide;
- An average of $136 is attributed to each phishing attack. In total, this amounts to $44.2 lost each year due to cybercriminals;
- Over 50% of IT decision-makers view phishing as a top security concern.

Key Takeaways
Email spoofing is a real concern. As time moves by, cybercriminals are finding newer and better ways of fooling users. To avoid being caught out, it’s important that you educate yourself on these dangers.
In this guide to email spoofing, we highlighted:
- The subtle (yet important) differences between spoofed emails and other, more generic phishing attacks
- The main motivations behind spoofing attacks, including spreading malware and avoiding block lists
- The three main types of spoofed email messages
- The essential ways to protect yourself and your domain from spoofing attacks
- Some of the most significant stats around email spoofing and why this can be incredibly dangerous.
Hopefully, you now have an understanding of spoofing and how you can protect yourself. Try to stick to the tips outlined in this article and take all the necessary steps to secure yourself online. But don’t take on this burden alone—share this article with your colleagues so that your entire team is aware of the tell-tale signs of email spoofing.
Also read: Email Deliverability: The Definitive Guide

